SECURE FILE
SHARING & E-SIGNATURE
REQUEST A DEMO
No one wakes up and thinks about file sharing. It’s not until the middle of tax season that file sharing bottlenecks are most evident when everything needs to be moving as smoothly as possible. There’s nothing worse than taking a 10-minute phone call to walk your client through the process of opening up a document. If they would just read the email you sent them containing the password then there wouldn’t be any problems, right?
WHAT IS SECURE FILE SHARING?
Secure Information
Despite your client’s difficulties, you need to secure their information. It’s a huge responsibility to handle the data involved with an accounting workflow and accountants face this task on a daily basis. The amount of data and security breaches, hacked emails, and stolen identities has increased 50% or more, every year, for the past four years. Before you think that you’re too small to be targeted, understand that hackers attack weakness, not size. They know that you don’t have the budget or resources to constantly have an entire IT team monitoring your technological security and infrastructure. Even if your server is encrypted, once you send emails externally, they are out in the open and vulnerable just like every other email.
Designed for all
You might already have a client portal that came with your tax software or the company that created your website. If you’re like the majority of accounting and finance firms we talk to, then you’re having difficulty with clients actually adopting the portal. Some clients will love their client portal account and will use it all the time, but those are rare. ImagineShare was created to satisfy every type of client, not just the tech-savvy ones.
It's the Law
At the end of the day, it’s the law. You have to secure your client’s information when sending to them. Even if they say it’s ok and you get the written permission of your client to send it unsecured, you’re still breaking the law. If you haven’t been securing information in the past and you’ve never had a data breach, then you’ve simply been lucky so far. Even if you’ve never been robbed, you still lock your doors at night. We’re at a point in modern technology where security is not a “nice to have”, it’s not something that you just do for the good of your clients, it’s a necessity for running a lawful and ethical business.
THE PROBLEM WITH THE STATUS QUO
The secret’s out, clients don’t like to use client portals. Your tax software told you that their client portal will be a great way to send and receive files with your clients, but it turns out that none of them actually use it! A handful of clients will like using a portal, but the majority of them would rather get their files through email, in person, or in their mailbox.
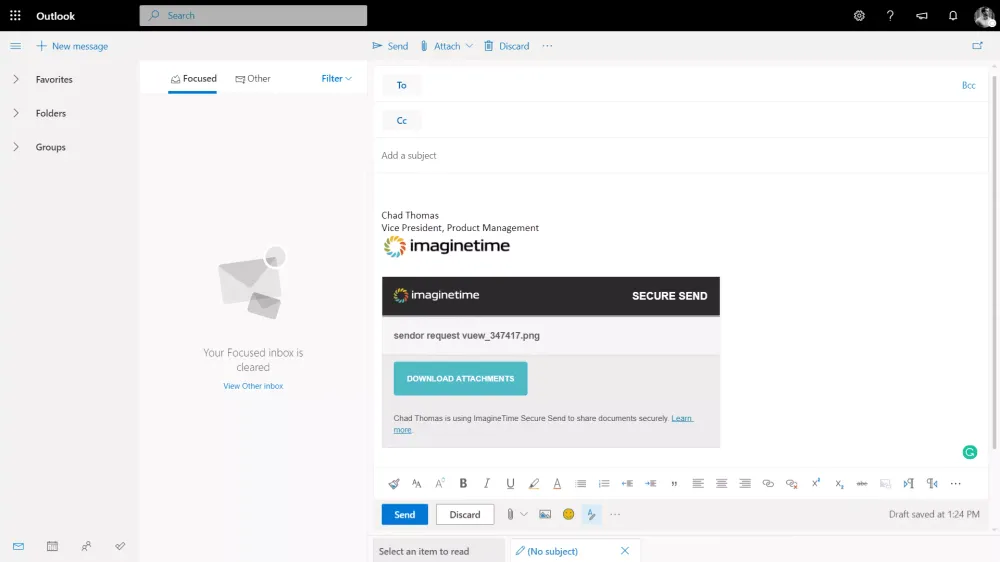
If you are emailing PII (Personally Identifiable Information), it needs to be secured by law. Most firms we talk to are password protecting the documents they send out which provides security, but only a minimal amount, and clients still have trouble opening the documents.
Does this sound familiar? You send them their password protected file, then send a second email or give them a call to let them know what the password is. Then they reply to your email or give you a call and tell you that they don’t know what their password is. This happens to every accounting firm, and it’s a result of a system that is built around the accountant, not around the client. Whether you’re sending the file through your client portal or through a password protected PDF, they still have to find out what the password is. That barrier to entry will stop your clients from adopting the technology you purchased and keeps your firm in the dark age.
Firms with paper-based methods (meeting in person, using the mail system) are stuck in the process for two reasons; it’s what you’ve always done and you haven’t offered anything easy enough for your clients to actually use. Very few firms are actually “paperless”, but most firms are looking to reduce the paper in their office. Making the transition from paper to digital happens gradually and requires effort on your part. Clients need to be reminded and trained with regularity, but you need to offer something that isn’t a pain to use at the same time.
Getting your client to sign their e-file authorization form is every accountant’s favorite pastime. The amount of follow-up calls and follow-up emails required to get documents signed and returned is ludicrous. There are more important things you or your staff can be doing instead. Getting client documents signed is difficult because it requires the client to meet up in person, mail things back to you, or have a printer/scanner/fax machine. All of those processes are very easy for your client to put off “until tomorrow”.
LEARN MORE ABOUT IMAGINESHARE
To learn more about ImagineShare and ImagineTime’s other practice management software features, contact sales and schedule your free demo with us today.
WHY DOES SECURE FILE SHARING MATTER?
Put your name on it, not ours.
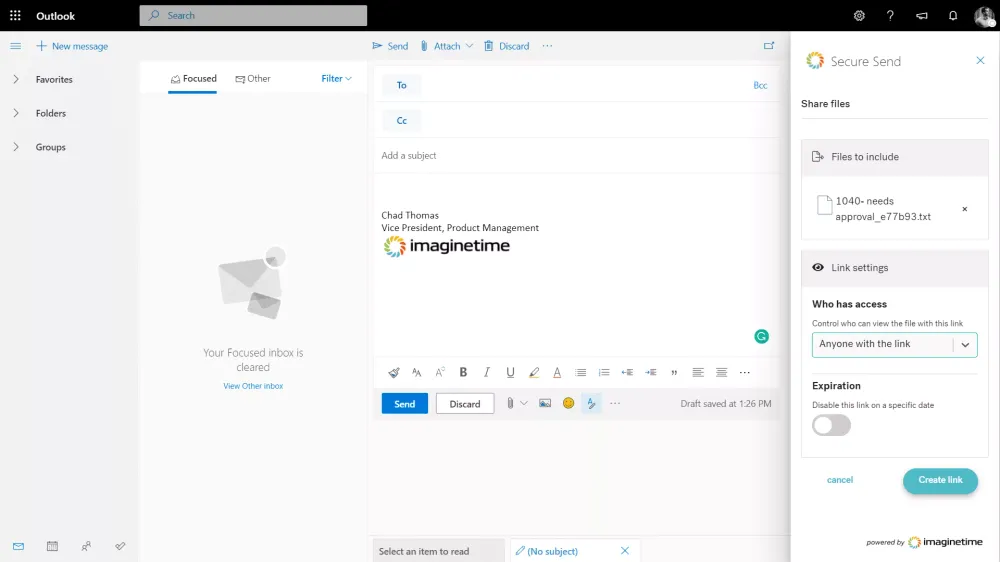
ImagineShare’s private label customization feature lets you apply your firm’s name, colors, and logo to the interface, so your clients are interacting with your custom branding, not ours.
Workflows
ImagineShare was designed around your workflow AND the client’s workflow. If you have tech-savvy clients who love the idea of a client portal for accountants, we provide that for you. If you have clients that have trouble with usernames and passwords, we provide a process that they can actually use. When it comes to clients and technology, one size does not fit all. ImagineShare has a blended approach to client file sharing that allows you to cater to different types of clients in a secure way. Getting documents signed through our e-signature platform expedites the entire process, saving you time and money.
Software that works the way you work.
Save time and streamline your workflow by enabling clients to receive and send secure files to and from your organization without changing the way you operate. ImagineShare is a file sharing solution that is easy to use without compromising on data security.
WHAT IS AN ELECTRONIC SIGNATURE?
The Electronic Signature & Records Association (“ESRA”) defines an electronic signature as: “an electronic sound, symbol or process that is attached to or logically associated with a record and executed or adopted by a person with the intent to sign the record.” In layman’s terms, an electronic signature a string of virtual fingerprints that are used to verify the identity of a signer and intent to sign the document.
Simple & fast
Build client signature requests into a streamlined workflow using ImagineTime’s e-signature module. Verify signer identity with Knowledge-Based Authentication (“KBA”), capture a legally binding signature, and securely store completed documents — all at the push of a button.
Upload & send
We are all familiar with the old-fashioned way of requesting client signatures: Print. Sign. Scan. Repeat. After all of the hard work preparing the required forms, this seemingly simple process can lead to agonizing delays. With ImagineTime’s e-signature module, you can get documents signed by your clients at anytime and from anywhere. You just upload the document and it is delivered to your client to sign instantly.
Legally binding
The Uniform Electronic Transactions Act (“UETA”) and the Electronic Signature in Global and National Commerce Act (“ESIGN”) provide legal guidelines for ensuring the validity of electronic records and documents signed online. Electronic signatures are legally binding if the following requirements are met:
The signer’s identity can be confirmed or authenticated using a digital marker, like an IP address.
The parameters of the transaction are communicated and the signer undeniably intended to undergo the method of signing.
The signature associated with the document is verifiable and has evidentiary documentation.
ImagineTime provides a digital audit trail that compiles the following unique identifying information so you can validate the identity of a signer and prevent tampering:
-IP addresses
-OS and browser information
-Geographic coordinates
-Time and date stamps